Getting Started
The following articles will guide you through the simplest path to issuing and verifying your first decentralized verifiable credentials (VC) using Partisia's My Data Activation (MDA). Before diving into the most exciting part -the product itself- let’s first explore why decentralized identities matter and the capabilities they unlock.
Why Decentralized Identities?
Decentralized identities, also known as Self-Sovereign Identities (SSI) or reusable IDs, are designed to give individuals full control over their digital identities and data without relying on centralized authorities. At the core of this concept is the principle that users own their personal data and can grant consent on a per-use basis.
In the simplest decentralized identity scenario, the holder (typically the end user) shares all the claims (e.g., age, height, nationality) contained in a verifiable credential, giving the verifier access to this information. As part of this simple presentation -and as in any other decentralized identity interaction- the verifier can easily confirm the credential’s integrity and authenticity without contacting the original issuer, thereby preserving the end user’s privacy.
Additionaly, on top of this basic flow, decentralized identities also support even greater privacy-enhancing options:
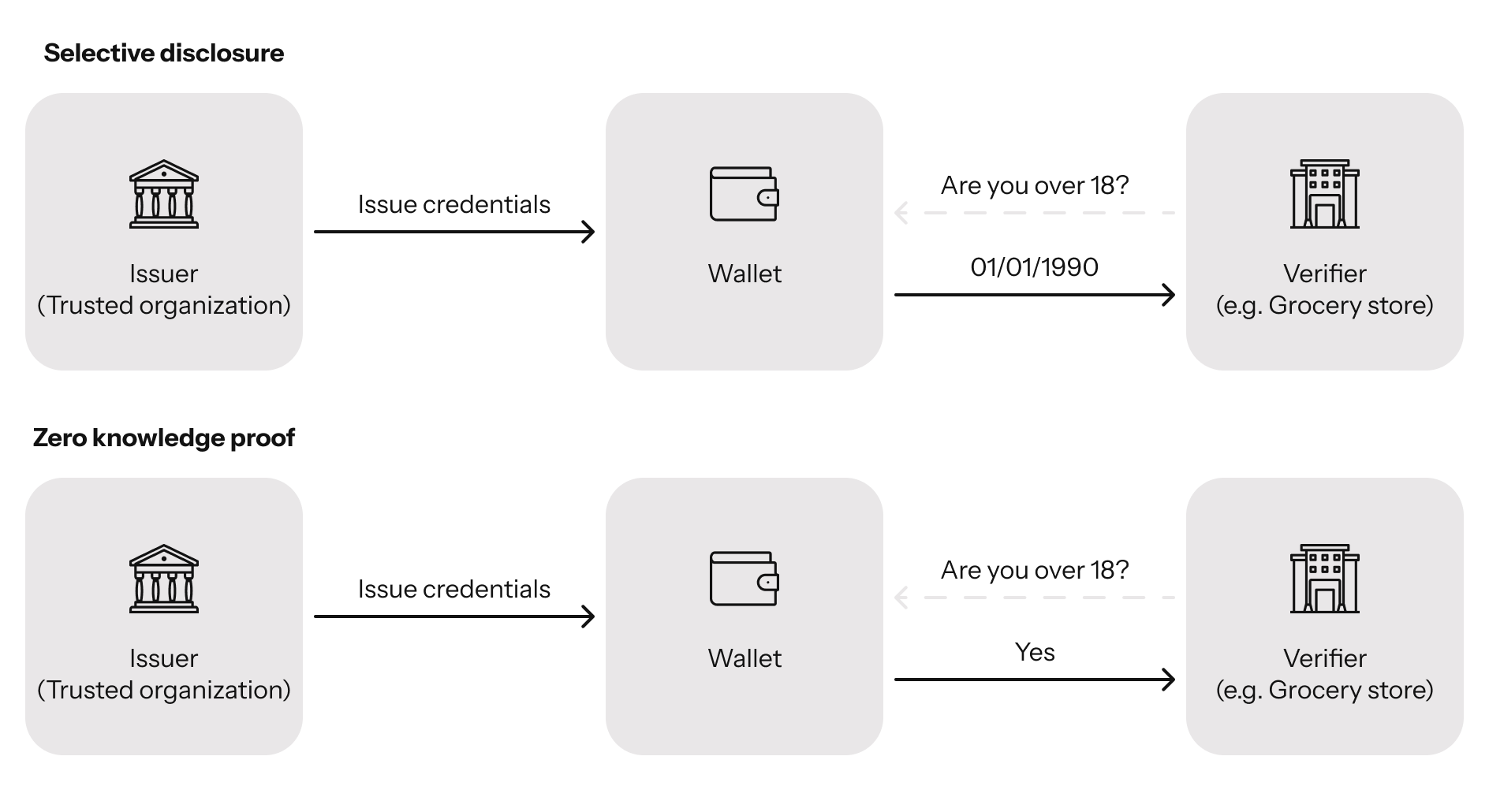
- Selective disclosure: Reveal only the exact attributes needed for a transaction -no oversharing of personal details.
- Zero-knowledge proofs: Prove statements (e.g., age > 18) without exposing the underlying data.
The following illustration shows the practical use of selective disclosure and zero-knowledge proofs: as the reader can notice, only the birthdate, or a simple yes/no is disclosed -not the entire credential or any additional information.
To sum up, decentralized identities are built with these principles in mind:
- Decentralized control: Ownership and management of verifiable credentials happen without reliance on any central authority that could surveil or control individuals.
- Native interoperability: Built on open standards such as W3C Verifiable Credentials Data Model v2.0, decentralized identities are designed to work seamlessly across diverse contexts and regions.
- Privacy-first approach: Leverage selective disclosure and zero-knowledge proofs to ensure only minimal necessary attributes are revealed, protecting users' privacy.
- Embedded trust: Use decentralized registries (for instance, blockchain-based) and cryptographic signatures so verifiers can independently confirm the authenticity and integrity of credentials without contacting the issuer.
Why Should Organizations Care?
- Regulatory drivers: EU regulations such as eIDAS 2.0 mandate adopting decentralized identities, requiring acceptance of digital wallets and verifiable credentials. With similar laws emerging globally, early adopters will achieve compliance faster and gain a competitive edge.
- Better user experience: Slow onboarding processes cause 48% of banks to lose clients. Decentralized identities allow users to reuse credentials across services, eliminating redundant checks, enhancing user experience, and boosting conversion.
- Enhanced efficiency: Traditional KYC checks are estimated to cost between $1,500 and $3,500 per verification, largely due to manual, repetitive compliance procedures. Decentralized identities are designed to improve efficiency by eliminating redundant checks, reducing compliance costs, and minimizing data-handling risks.
What Are Verifiable Credentials?
Verifiable credentials are tamper‑evident digital credentials -also referred to as cryptographically verifiable assertions or digital attestations- that contain claims about a subject (e.g., name, age, qualification). Each credential is:
- Issued by a trusted entity -the issuer-, digitally signed to ensure authenticity.
- Held by the subject in a digital wallet -the holder-, giving them full control over when and how to share it.
- Verified by any third party -the verifier- through cryptographic checks against verifiable data registries (without contacting the issuer directly).
Verifiable credentials are cryptographically secure and tamper-evident, providing a trustworthy way to exchange data and making them well-suited for digital identity management and asynchronous data sharing. You can read more about them here.
Prerequisites
At Partisia, we believe in empowering companies and their users to truly own their data without creating unnecessary dependencies. That’s why the Partisia platform is designed to run on‑premises -not as a Software‑as‑a‑Service (SaaS) application. To run this solution, you’ll need to understand how to deploy and configure its various components.
To unlock the full potential of Partisia’s My Data Activation, you need a valid license for the Partisia Platform. Please book a call with us to obtain yours.
Why Not SaaS?
At Partisia, we believe individuals and organizations should retain ownership and control of their sensitive data. Many SaaS platforms compromise that principle by implementing unnecessary centralized management -a model that brings several drawbacks:
-
Weakened data ownership: Your data will be stored -or at least processed- on the SaaS provider’s servers, limiting your ability to fully control it, audit its usage, or easily migrate it elsewhere.
-
Vendor lock‑in: Transferring your credentials, identities, or audit logs from a SaaS solution can be challenging, often requiring custom scripts or manual work. You typically won’t have direct access to all the necessary resources to easily switch providers.
By choosing a self-hosted, decentralized solution like the Partisia platform, organizations regain full data sovereignty, transparent governance, and seamless interoperability -without sacrificing ease of use.