Building Trusted Ecosystems
Can you imagine a world where digital services and applications can’t be trusted? It would be a risky and unstable place to live.
Decentralized identities and verifiable credentials enable companies and organizations to create or rely on trust-by-design ecosystems. 'Trust by design' means embedding cryptographic guarantees, user control, and transparent governance into the very fabric of these ecosystems -rather than bolting on security as an afterthought.
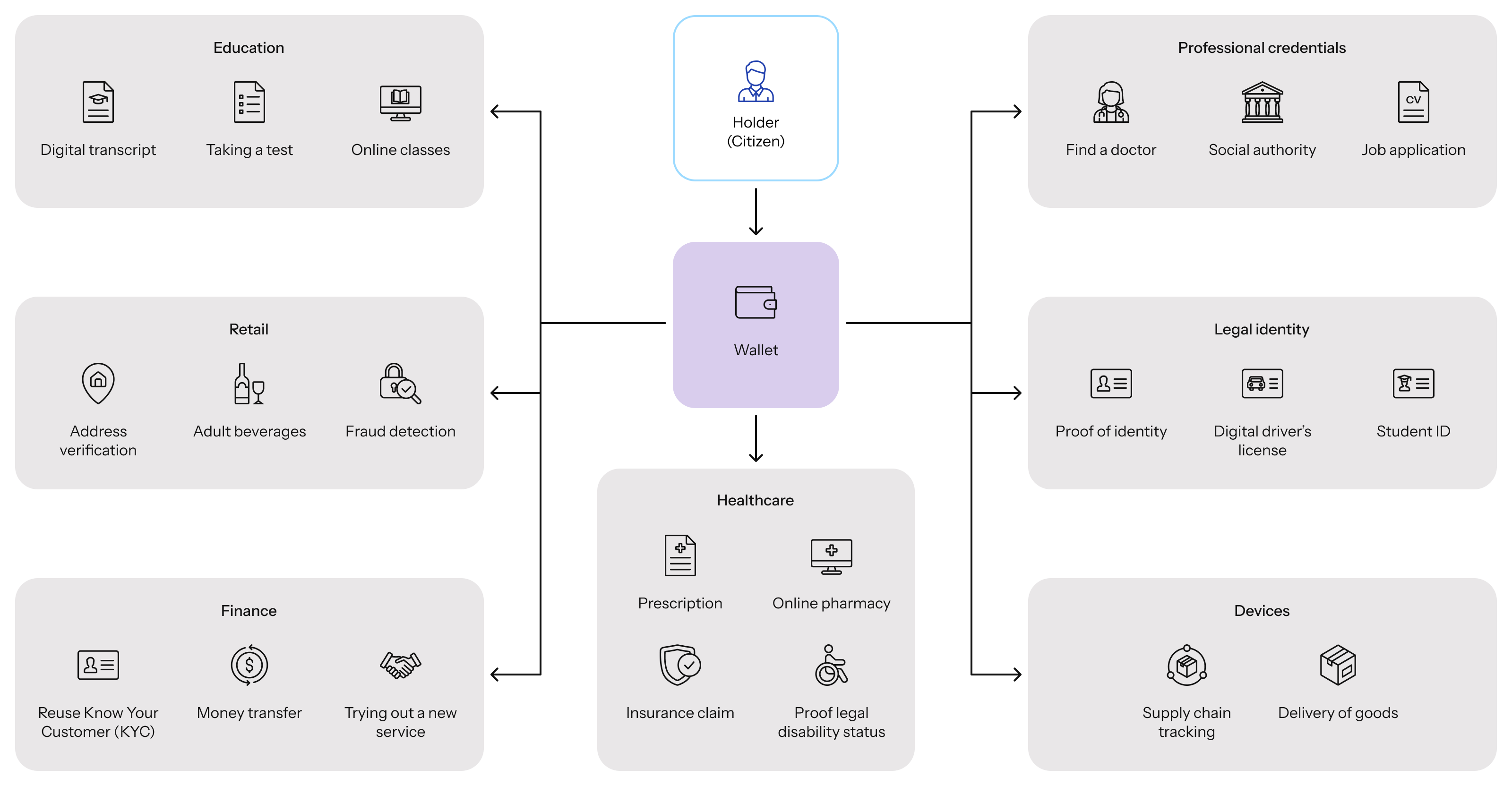
Trusted ecosystems, enabled by verifiable credentials and decentralized identities, are rapidly emerging and will soon be widely accessible, enabling people to benefit from them across a wide range of use cases:
Partisia’s My Data Activation (MDA) helps organizations create or integrate with trusted digital ecosystems by enabling them to seamlessly issue, manage, and verify credentials. Key characteristics of such ecosystems include:
-
Use of verifiable credentials: Verifiable credentials are used to ensure that every interaction is cryptographically sound and tamper‑evident. Verifiers -also known as relying parties- can confirm data authenticity without centralized gatekeepers.
-
Individual empowerment: Individuals retain full ownership of their sensitive data. In decentralized ecosystems, users decide what to share, with whom, and for how long -fostering trust and transparency in digital interactions.
-
Extended interoperability: By adhering to open standards, companies and organizaitons can unlock network effects and avoid vendor lock‑in.
-
Increased transparency and security: Distributed governance models reduce single points of failure and enhance auditability, increasing system resilience.
Decentralized vs Centralized
Decentralized identities enhance privacy, security, and transparency by breaking down barriers between siloed systems and giving users true ownership of their digital identities.
| Aspect | Centralized Model | Decentralized Model |
|---|---|---|
| Data Ownership | Held by a central authority; subject to surveillance and unilateral policy changes. | Controlled by users, who grant access and consent on a per-use basis. |
| Privacy & Security | High risk of large-scale data breaches; limited transparency. | Privacy-preserving through selective disclosure and zero-knowledge proofs. |
| Scalability | Vertical scaling; costly infrastructure upgrades; vendor lock-in. | Open networks drive adoption. |
| Interoperability | Proprietary protocols; integration overhead. | Open standards enable plug-and-play integration across regions. |
| Resilience | Single points of failure; downtime impacts all users. | Distributed consensus and redundancy mitigate outages and censorship. |